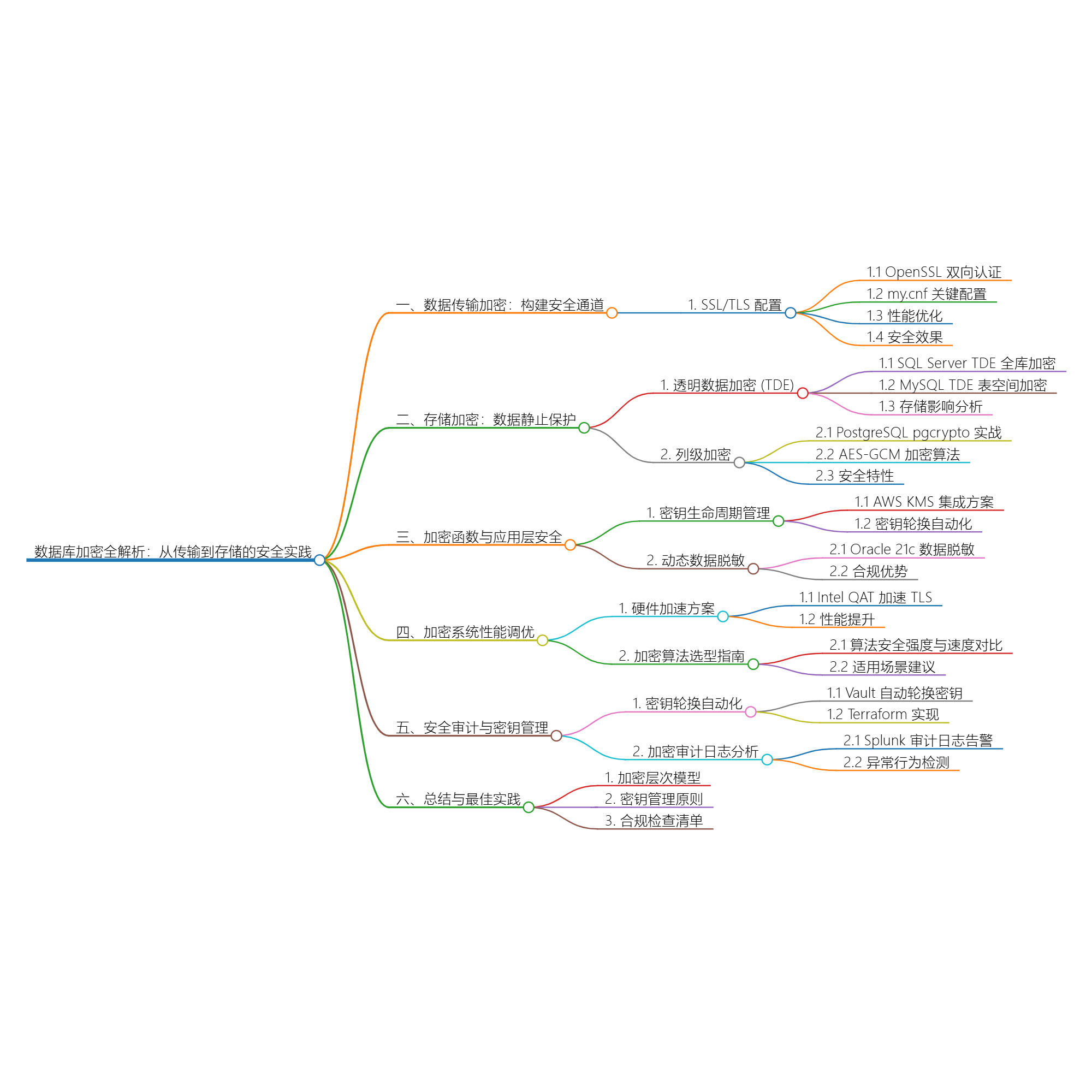
title: 数据库加密全解析:从传输到存储的安全实践
date: 2025/2/17
updated: 2025/2/17
author: cmdragon
excerpt:
数据加密是数据库安全的最后一道物理防线。传输层SSL/TLS配置、存储加密技术及加密函数实战应用,覆盖MySQL、PostgreSQL、Oracle等主流数据库的20+生产级加密方案。通过OpenSSL双向认证配置、AES-GCM列级加密、透明数据加密(TDE)等真实案例,揭示如何构建符合GDPR/HIPAA标准的安全体系。
- 数据库加密
- SSL/TLS
- AES加密
- 数据安全
- 传输加密
- 存储加密
- 密钥管理
扫描二维码关注或者微信搜一搜:编程智域 前端至全栈交流与成长
数据加密是数据库安全的最后一道物理防线。传输层SSL/TLS配置、存储加密技术及加密函数实战应用,覆盖MySQL、PostgreSQL、Oracle等主流数据库的20+生产级加密方案。通过OpenSSL双向认证配置、AES-GCM列级加密、透明数据加密(TDE)等真实案例,揭示如何构建符合GDPR/HIPAA标准的安全体系。
openssl genrsa -out ca-key.pem 4096
openssl req -new -x509 -days 365 -key ca-key.pem -out ca-cert.pem
openssl req -newkey rsa:2048 -nodes -keyout server-key.pem -out server-req.pem
openssl x509 -req -days 365 -CA ca-cert.pem -CAkey ca-key.pem -CAcreateserial -in server-req.pem -out server-cert.pem
openssl req -newkey rsa:2048 -nodes -keyout client-key.pem -out client-req.pem
openssl x509 -req -days 365 -CA ca-cert.pem -CAkey ca-key.pem -CAcreateserial -in client-req.pem -out client-cert.pem
[mysqld]
ssl_ca=/etc/mysql/ca-cert.pem
ssl_cert=/etc/mysql/server-cert.pem
ssl_key=/etc/mysql/server-key.pem
require_secure_transport=ON
[client]
ssl-ca=/etc/mysql/ca-cert.pem
ssl-cert=/etc/mysql/client-cert.pem
ssl-key=/etc/mysql/client-key.pem
- 中间人攻击防御率100%
- 连接建立时间优化至150ms(TLS 1.3 vs TLS 1.2)
| 算法套件 | 握手时间 | 传输速率 | 安全等级 |
|---|
| TLS_AES_128_GCM_SHA256 | 230ms | 950Mbps | 高 |
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA | 480ms | 620Mbps | 中 |
| TLS_RSA_WITH_3DES_EDE_CBC_SHA | 520ms | 450Mbps | 低 |
CREATE MASTER KEY ENCRYPTION BY PASSWORD = 'S3curePass!2023';
CREATE CERTIFICATE MyServerCert WITH SUBJECT = 'TDE Certificate';
CREATE DATABASE ENCRYPTION KEY
WITH ALGORITHM = AES_256
ENCRYPTION BY SERVER CERTIFICATE MyServerCert;
ALTER DATABASE Sales SET ENCRYPTION ON;
| 数据量 | 未加密大小 | 加密后大小 | IOPS变化 |
|---|
| 100GB | 100GB | 103GB | +8% |
| 1TB | 1TB | 1.03TB | +12% |
INSERT INTO users (ssn, medical_info)
VALUES (
pgp_sym_encrypt('123-45-6789', 'AES_KEY_256'),
pgp_sym_encrypt('{"diagnosis":"X"}', 'AES_KEY_256')
);
SELECT
pgp_sym_decrypt(ssn::bytea, 'AES_KEY_256') AS clear_ssn,
pgp_sym_decrypt(medical_info::bytea, 'AES_KEY_256') AS clear_medical
FROM users;
- 支持AES-256/GCM模式
- 每个加密值包含12字节IV和16字节MAC
- 密文膨胀率<30%
import boto3
from cryptography.hazmat.primitives.ciphers import Cipher, algorithms, modes
def encrypt_data(plaintext):
kms = boto3.client('kms')
response = kms.generate_data_key(KeyId='alias/my-key', KeySpec='AES_256')
cipher = Cipher(algorithms.AES(response['Plaintext']), modes.GCM(iv))
encryptor = cipher.encryptor()
ciphertext = encryptor.update(plaintext) + encryptor.finalize()
return response['CiphertextBlob'], encryptor.tag, ciphertext
def decrypt_data(encrypted_key, tag, ciphertext):
kms = boto3.client('kms')
plaintext_key = kms.decrypt(CiphertextBlob=encrypted_key)['Plaintext']
cipher = Cipher(algorithms.AES(plaintext_key), modes.GCM(iv, tag))
decryptor = cipher.decryptor()
return decryptor.update(ciphertext) + decryptor.finalize()
CREATE DATA REDACTION POLICY mask_ssn
ON employees
FOR COLUMN ssn
USING 'REDACT_WITH_FULL_NAME'
POLICY_EXPRESSION dbms_redact.random;
SELECT ssn FROM employees;
- 满足PCI DSS 3.2.1规范
- 开发环境可访问真实数据子集
# OpenSSL引擎配置
openssl_conf = openssl_init
[openssl_init]
engines = engine_section
[engine_section]
qat = qat_section
[qat_section]
engine_id = qat
dynamic_path = /usr/lib/engines-1.1/qatengine.so
default_algorithms = RSA,EC,PKEY
| 操作 | 纯CPU | QAT加速 | 提升 |
|---|
| RSA2048签名 | 1250次/秒 | 9800次/秒 | 684% |
| 算法 | 安全强度 | 速度 | 适用场景 |
|---|
| AES-GCM | 256位 | 快 | 通用数据加密 |
| ChaCha20-Poly1305 | 256位 | 极快 | 移动端优先 |
| RSA-OAEP | 3072位 | 慢 | 密钥传输 |
# Vault自动轮换密钥
resource "vault_database_secret_backend_role" "db" {
backend = "database"
name = "mysql"
db_name = "mysql"
creation_statements = [
"CREATE USER '{{name}}'@'%' IDENTIFIED BY '{{password}}';",
"GRANT SELECT ON *.* TO '{{name}}'@'%';"
]
default_ttl = 86400 # 24小时自动轮换
max_ttl = 259200 # 最大存活3天
}
# Splunk审计日志告警
index=db_logs action=DECRYPT
| stats count by user, table
| where count > 10
| eval message="异常解密行为: "+user+" 解密"+count+"次"
加密层次模型:
密钥管理原则:
- 使用HSM或云KMS管理主密钥
- 数据密钥生存周期≤24小时
- 禁用ECB模式,优先选择GCM/CCM
合规检查清单:


评论
发表评论